Use Tokens as your Authentication Provider
Okteto defaults to token-based authentication to simplify the installation and configuration of Okteto self-hosted.
In this mode, Okteto automatically generates a token for an Admin user that you can use to log in to the Okteto UI and start exploring Okteto's features and functionality much faster than configuring other authentication methods. Once you've completed the product evaluation, we recommend switching to another authentication method for your final rollout. Token-based authentication is not ideal for production use of Okteto.
To use token-based authentication, remove the auth section of your Okteto Helm configuration file and upgrade your Okteto instance for the new configuration to be applied.
Then, follow our post-installation notes to learn how to login to the Okteto UI and configure your Okteto CLI with a randomly generated token.
After you log in, you can also invite other users by generating an "Invitation Link" from the Admin -> Users page of the Okteto Dashboard. This option allows you to grant access to other users to continue your evaluation.
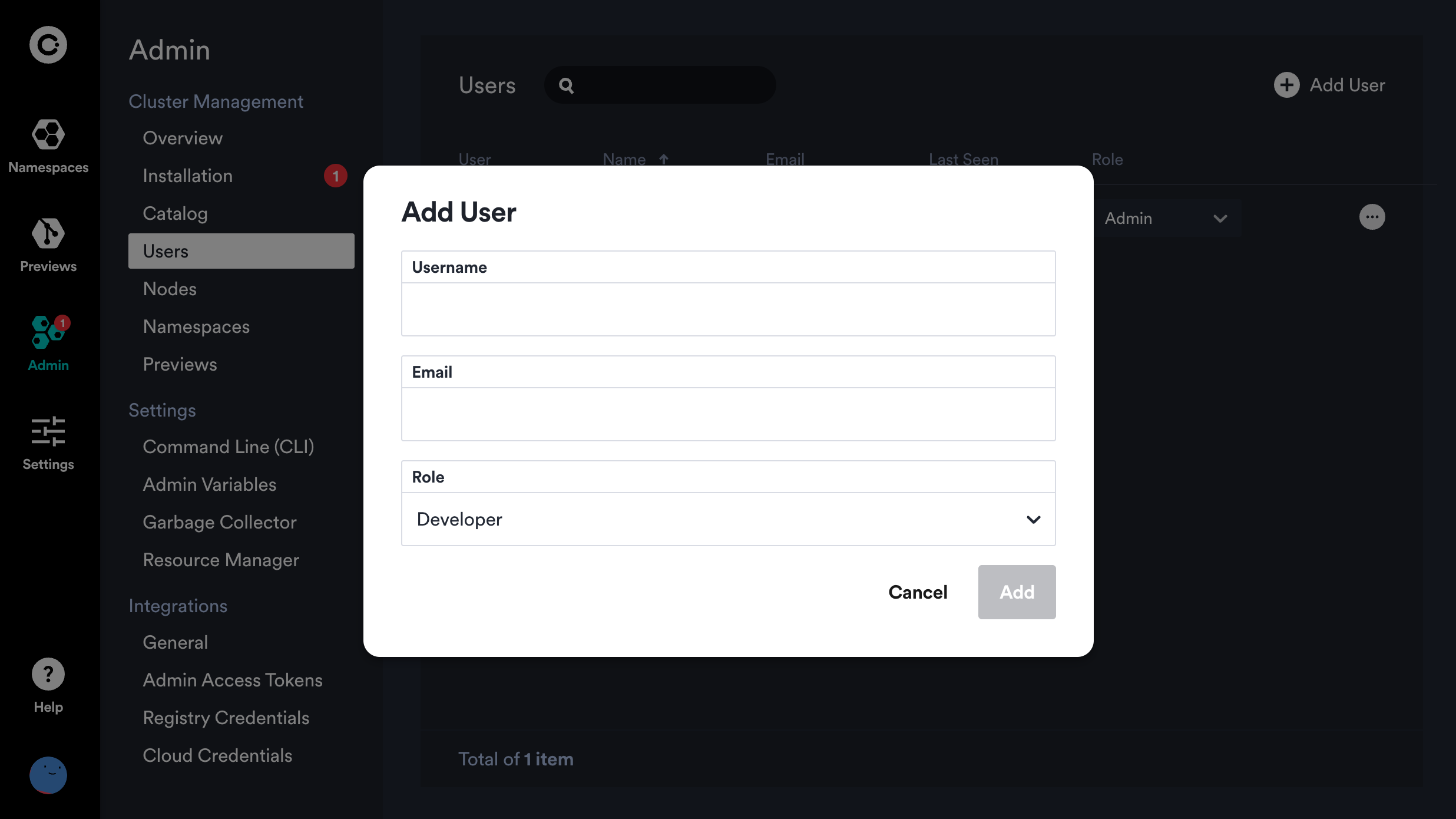
An invitation link will be generated that can be shared with the intended user via a secure method. Please note that Okteto does not send invite emails automatically.
Once the the user has opened the invitation link, they can copy their Okteto token and see details on how to connect the Okteto CLI.
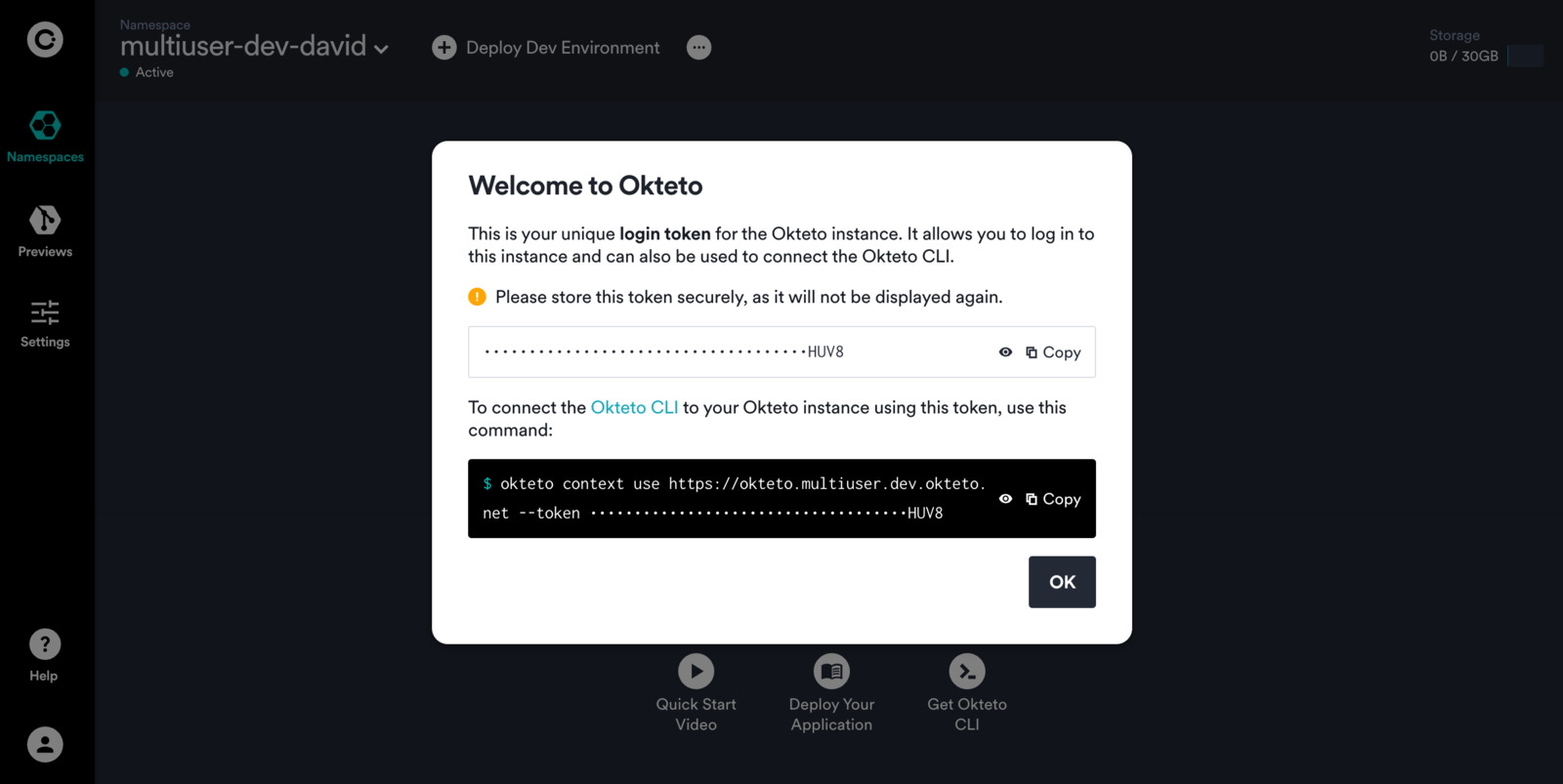
After successful use, the invite link becomes invalid.
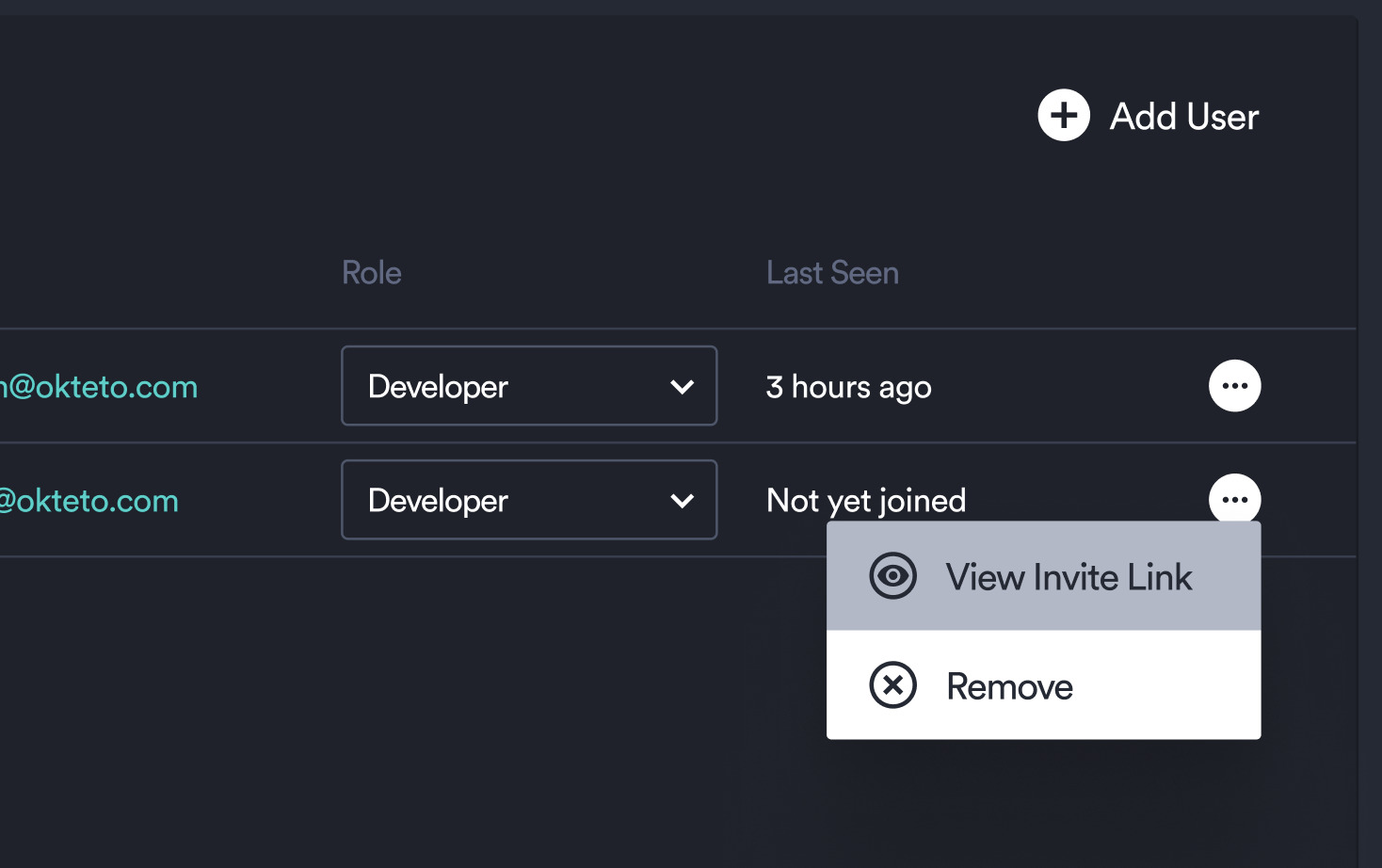
If for any reason a user has not yet joined your Okteto instance and cannot find the invitation, the link can be viewed again by an administrator. To do so, click on the three dots related to the invited users name, then select "View Invite Link."
Retrieve a User's Token
Okteto generates "Invitation Links" in Token Auth mode to allow other users to log in to Okteto. When a user logs in to Okteto via the Invitation Link, a "Welcome screen" is presented showing the user's token. This token can be used to log in from the Okteto UI or using the Okteto CLI.
The "Welcome screen" prompts the user to store this token securely.
In the event of losing this token, the cluster admin can retrieve the token of a given username by executing the following command:
kubectl get sa -l=dev.okteto.com/external-id=<username> -o=jsonpath='{.items[0].metadata.labels.dev\.okteto\.com/token}'